by The Same Day Computer Team | Nov 7, 2017 | Blog, Front Page, Laconia, News, Services, Upgrades, What We Do
a text message, it is being delivered right through an internet search! How it works: Hackers create multiple malicious websites that show up at the top of the search engines when you look for your bank. When you click on the one you think is correct, you are...
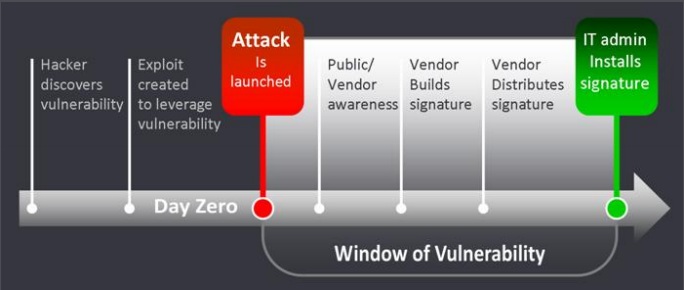
by The Same Day Computer Team | Nov 6, 2017 | Blog, Front Page, Laconia, News, Services, Uncategorized, Upgrades, What We Do
Zero-Day Exploits refers to a vulnerability in software that hackers have found and before the software company finds it and comes up with patch to fix it. This is not rare. Hackers are smart, otherwise they wouldn’t make money! A lot of the time software developers...

by The Same Day Computer Team | Nov 3, 2017 | Blog, Front Page, Laconia, News, Services, Uncategorized, What We Do
Ransomware is any software that encrypts your data until a sum of money is paid. There are a few different ways ransomware gets installed: 1: Drive by downloads 2: Clicking on an attachment in an email 3: Websites with Trojans that you may come across accidentally How...

by The Same Day Computer Team | Nov 2, 2017 | Blog, Front Page, Laconia, News, Services, Uncategorized, Upgrades, What We Do
Viruses are malware, or malicious software, that spreads through your computer and multiplies as it goes. They can slow your computer down, corrupt files, even corrupt the operating system, making it impossible to use your computer. While viruses, generally speaking,...

by The Same Day Computer Team | Nov 1, 2017 | Blog, Front Page, Laconia, News, Services, Uncategorized, Upgrades, What We Do
Malware is a very broad term. Basically, it is software that is software that is created to damage your system and/or to get your personal information. A smaller section of malware is malvertisting. This is an ad online with code in it so when you click on the image...

by The Same Day Computer Team | Oct 31, 2017 | Blog, Front Page, Laconia, News, Services, Uncategorized, Upgrades
This is a newer term than phishing but still one we have all heard. Pharming: While similar to phishing it is different. This is a where hackers make a convincing looking website or ad. After clicking on the website or ad they request your log in information and...





